Overview
Single sign-on allows you to log in using your company credentials. Unit single sign-on (SSO) is based on SAML 2.0. Unit works with Okta as well as other enterprise identity management platforms such as Google Workspace, Microsoft Active Directory, and many others.
Unit acts as the Service Provider (SP), and offers automatic user sign-in. Once Unit receives a SAML response from the Identity Provider (IdP), Unit checks if this user exists: If a user is found, the sign in succeeds.
NOTE
SSO does not provide automatic user provisioning in Unit. In order to log in to Unit via SSO, user provisioning can be achieved by using SCIM. Alternatively, you must first sign up to Unit dashboard with the same email address that you use with your identity provider.
Prerequisites
- Active Organization
- Admin privileges
Configuring SSO
SSO can be configured on the Org Settings section of the dashboard.
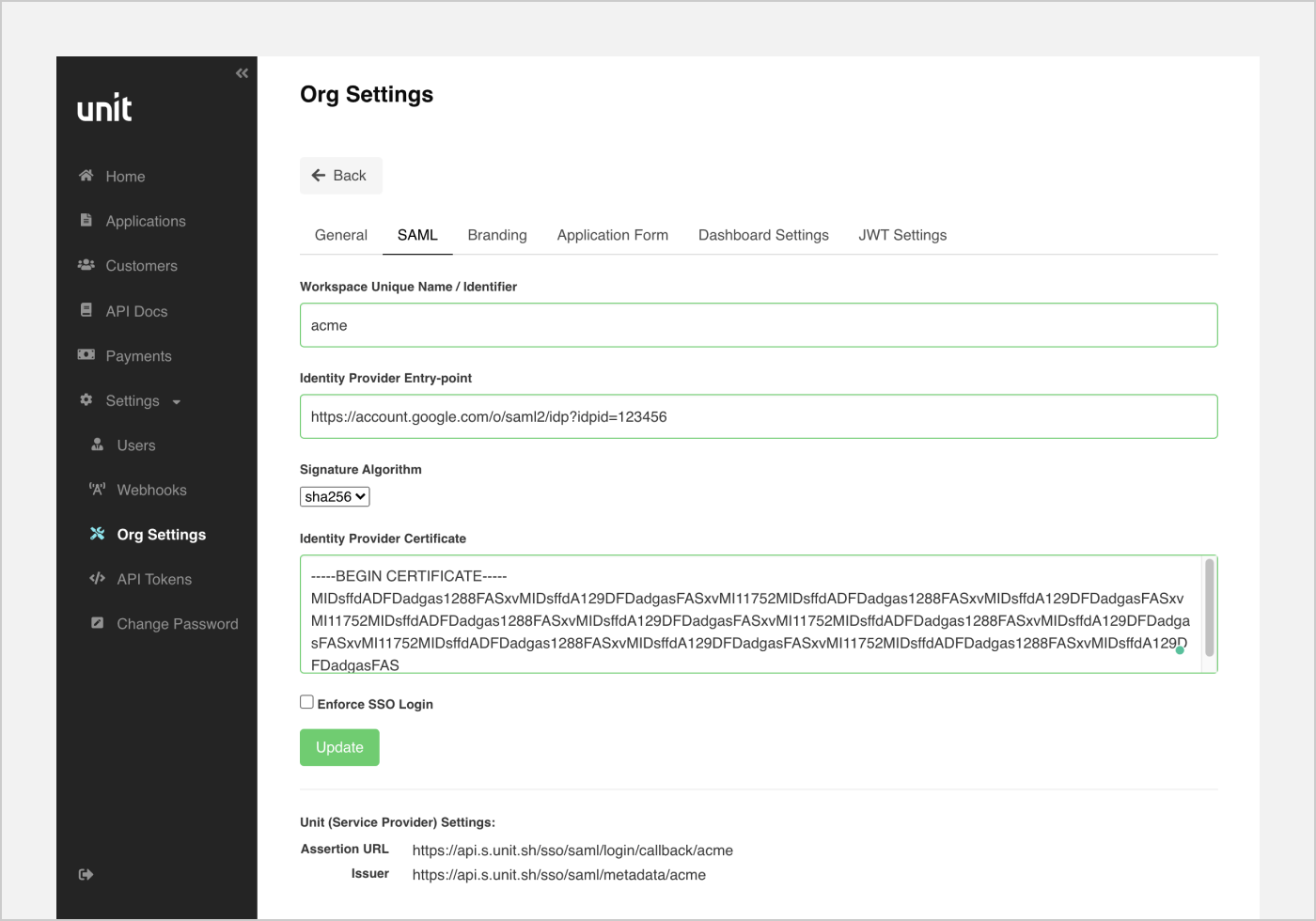
- Workspace Unique Name / Identifier: A simple unique name / identifier for your settings based on the org's name. Special characters are not allowed. This name will be used as an identifier for the Org's settings on SSO login attempt.
- Identity Provider Entry-point: Identity Provider URL to which the user will be redirected to during the sign in process.
- Signature Algorithm: Based on the identity provider's requirements.
- Identity Provider Certificate: A certificate generated by identity provider for the specified SAML settings.
- Enforce SSO Login: If selected, the SSO method will be the only option to login to the Unit dashboard.
- Assertion URL: Required by Identity Provider. The address where the user will be redirected after successful identification process. This URL is unique and based on your workspace name.
- Issuer: Required by Identity Provider. Unique identifier based on your workspace name.
Okta with Unit
A connection can be made between Okta (the identity provider) and Unit (the service provider), to allow users to connect to their Unit accounts.
To configure Okta as your identity provider with Unit, follow the following steps:
- From the Okta admin dashboard click on the SSO app link. Then click on Create App Integration and select SAML 2.0.
- Provide General Settings and click Next. Then Provide relevant SAML settings according to the following table. Attribute Statements email is required.
| Okta field | Unit field |
|---|---|
| Single sign on URL | Assertion URL |
| Audience URI (SP Entity ID) | Issuer |
- Add Email as an attribute statement

Click on Preview the SAML Assertion to verify that assertion XML is correct and contains all relevant attributes and properties.
By clicking Next and Finish you will be redirected to the Sign-On settings. Click on the View Setup Instructions button.
Click the View Setup Instructions button and copy relevant fields (see field mapping below) from the How to Configure SAML 2.0 for Application page to the Unit dashboard / Org Settings / SAML tab.
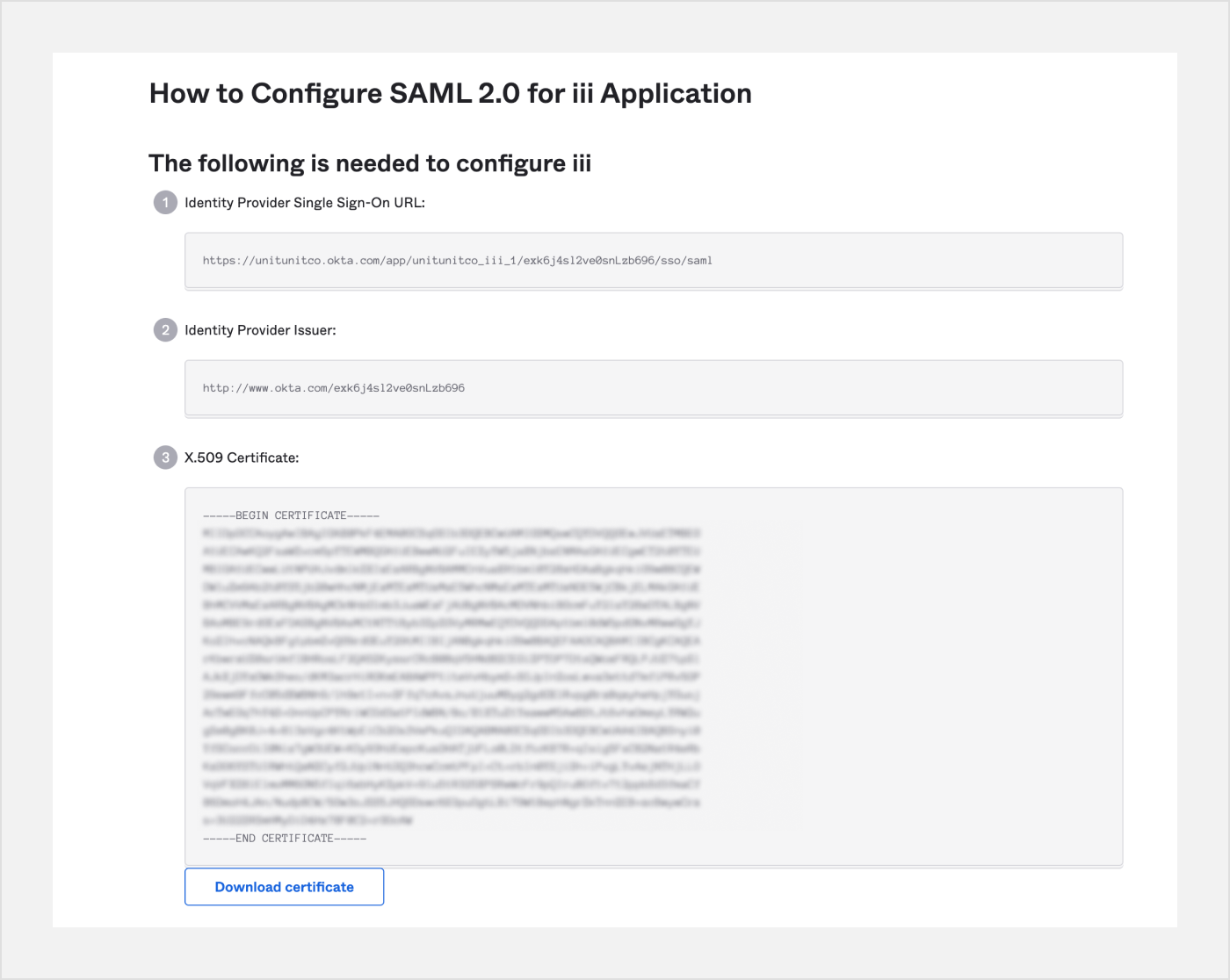
| Okta field | Unit field |
|---|---|
| Identity Provider Single Sign-On URL | Identity Provider Entry-point |
| X.509 Certificate | Identity Provider Certificate |
From app settings use Assign Users to App button to assign relevant users to the application.
Verify that the Signature Algorithm both on Okta and on Unit is set to sha256.
Azure Active Directory with Unit
A connection can be made between Azure (the identity provider) and Unit (the service provider), to allow users to connect to their Unit accounts.
To configure Azure as your identity provider with Unit, follow the following steps:
- Click on New Application on Active Directory / Enterprise applications menu and then on Create your own application>Integrate any other application you dob"t find in the gallery (Non-gallery).


- Once created select Set up single sign on from app properties page and then SAML box.

- Edit Basic SAML Configuration with the required URLs from the Unit dashboard:
| Active Directory field | Unit field |
|---|---|
| Identifier (Entity ID) | Issuer |
| Reply URL (Assertion Consumer Service URL) | Assertion URL |
- Verify that Attributes & Claims are identical to the following and delete all other entries:
email: user.userprincipalname
Unique User Identifier: user.userprincipalname

- Copy and past relevant fields from Azure to Unit SSO settings
| Unit field | Active Directory field |
|---|---|
| Identity Provider Entry-point | Login URL |
| Identity Provider Certificate | Certificate (Base64) |

Use Users and groups section to assign relevant users to the application.
Verify that the Signature Algorithm both on Azure and on Unit is set to sha256.
Google Workspace with Unit
A connection can be made between Google Workspace (the identity provider) and Unit (the service provider), to allow users to connect to their Unit accounts.
To configure Google Workspace as your identity provider with Unit, follow the following steps:
- Select the Web and mobile apps from Google Admin / Apps tab and then Add custom SAML app.
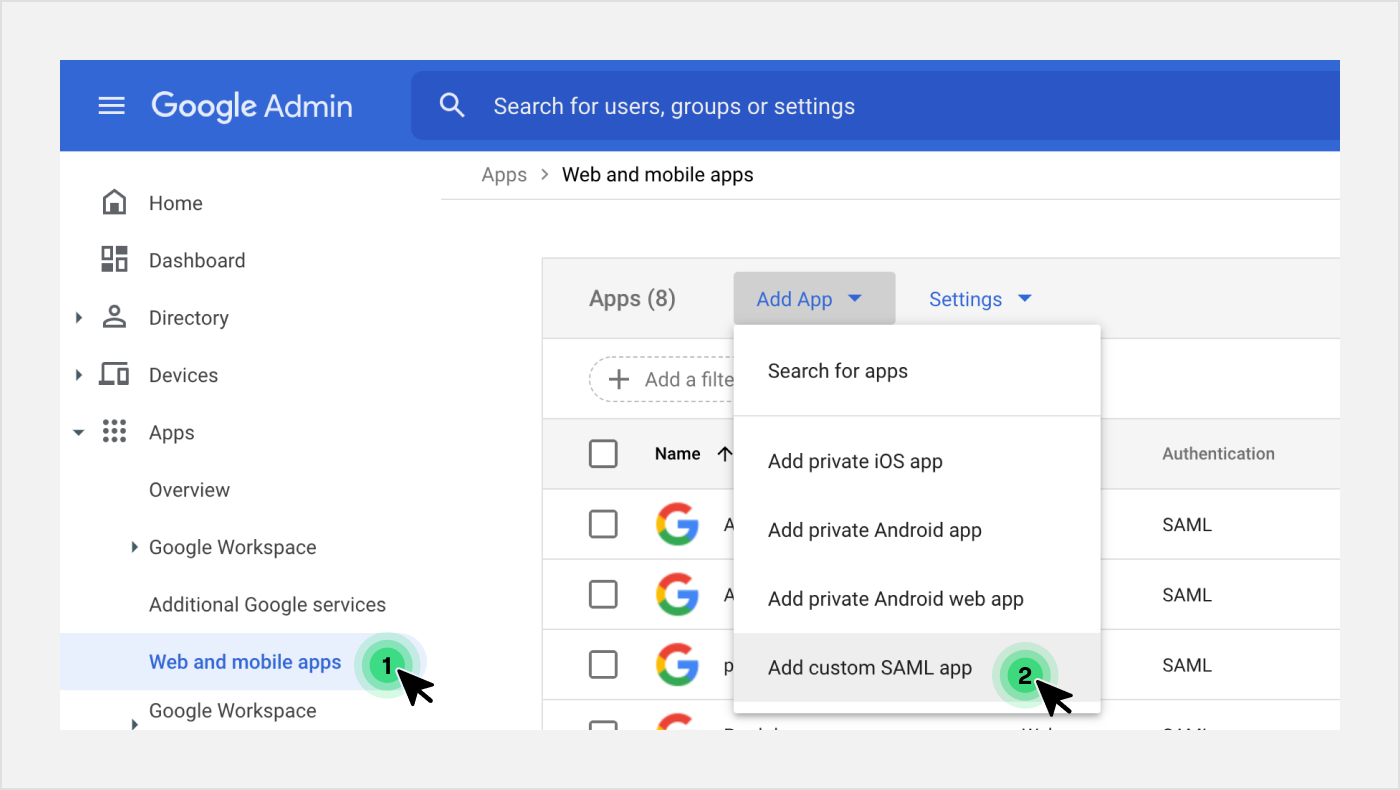
- You'll then see your specific Identity Provider information. Copy all relevant fields to the Unit dashboard / Org Settings / SAML tab.
| Google field | Unit field |
|---|---|
| SSO URL | Identity Provider Entry-point |
| Certificate | Identity Provider Certificate |
- Edit Service provider details with the required URLs from the Unit dashboard/Org Settings>SAML:
| Google field | Unit field |
|---|---|
| ACS URL | Assertion URL |
| Entity ID | Issuer |
- Verify that Name ID & Name ID format are similar to the following:

- Configure proper attributes mapping.
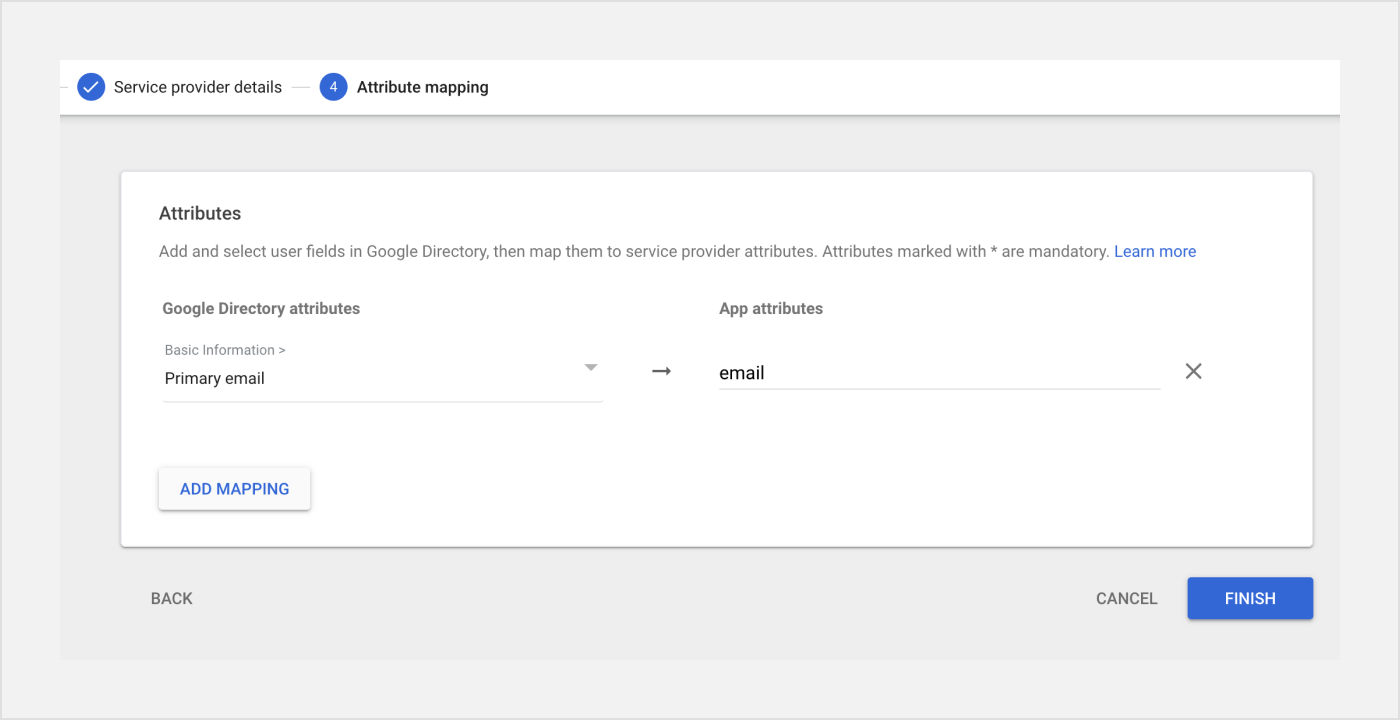
- Verify that the Signature Algorithm both on Google Workspace and on Unit is set to sha256.
